Implementing Mutual Transport Layer Security (mTLS)
Learn how to generate, request, and use certificates to securely authenticate with VTEX services using mTLS.
This feature is part of VTEX Shield. If you're already a VTEX client and would like to adopt VTEX Shield for your business, contact our Commercial Support. Additional fees may apply. If you're not yet a VTEX client but are interested in this solution, complete our contact form.
When making requests to VTEX services using mTLS, VTEX validates whether the certificate was issued and signed by its internal Certificate Authority (CA). This guide walks you through the process of obtaining and managing certificates for mTLS authentication.
Step 1 - Generating a Certificate Signing Request (CSR)
The first step is to generate a Certificate Signing Request (CSR) using OpenSSL 3.0.0 or higher. This process generates the CSR (.csr) and private key (.key) files.
Open a terminal and run the command below, replacing the values in {{ }} with your specific information:
_10openssl req -new -subj "/CN={{APP_NAME}}/OU={{TENANT}}/L={{CITY}}/ST={{STATE}}/C={{COUNTRY:2CHARS}}" -out APP_CERT_REQUEST.csr -nodes -sha512 -newkey rsa:2048 -keyout APP_CERT_PRIVATE_KEY.key
The fields CN (Common Name) and OU (Organizational Unit) are mandatory and must contain the application name and account name, respectively.
Save both generated files (.csr and .key) for the next step.
Step 2 - Issuing a certificate signed by VTEX
Once you've generated the CSR, use the POST Sign certificate endpoint to request a certificate signed by VTEX's Certificate Authority. This request allows you to submit a CSR and receive a signed certificate.
Required permission
To use this endpoint, your user or API key must have access to the following License Manager resource. Otherwise, a 403 status code error will be returned.
| Product | Category | Resource |
|---|---|---|
| CDN API | Certificate management | Update certificate |
There are no predefined roles for these resources. To use this endpoint, you must create a custom role and add the above resource. Learn more about roles and resources in the Roles documentation.
Request example
The request body should contain the previously generated CSR as plain text:
_10curl --request post \_10 --url https://apiexamples.vtexcommercestable.com.br/api/edge/private-certificates/sign \_10 --header 'Content-Type: text/plain' \_10 --header 'X-VTEX-API-AppKey: ' \_10 --header 'X-VTEX-API-AppToken: ' \_10 --data '-----BEGIN CERTIFICATE REQUEST-----_10***_10-----END CERTIFICATE REQUEST-----_10'
The account in the request must match the one specified in the
OUfield of the CSR.
Response
If successful, the API responds with the certificate in plain text:
_10-----BEGIN CERTIFICATE-----_10***_10-----END CERTIFICATE-----
Save this content to a .crt file. You'll use it along with the private key (.key) to authenticate requests.
Learn more in the
POSTSign certificate API reference.
Step 3 - Making requests with the certificate
With the certificate issued, you can now authenticate your requests to VTEX using mTLS. See examples using Postman and cURL below.
Using Postman
To test mTLS requests with Postman, attach your certificate and private key directly in the tool's settings. Follow the steps below:
- Open Postman and go to Settings.
- Navigate to the Certificates tab.
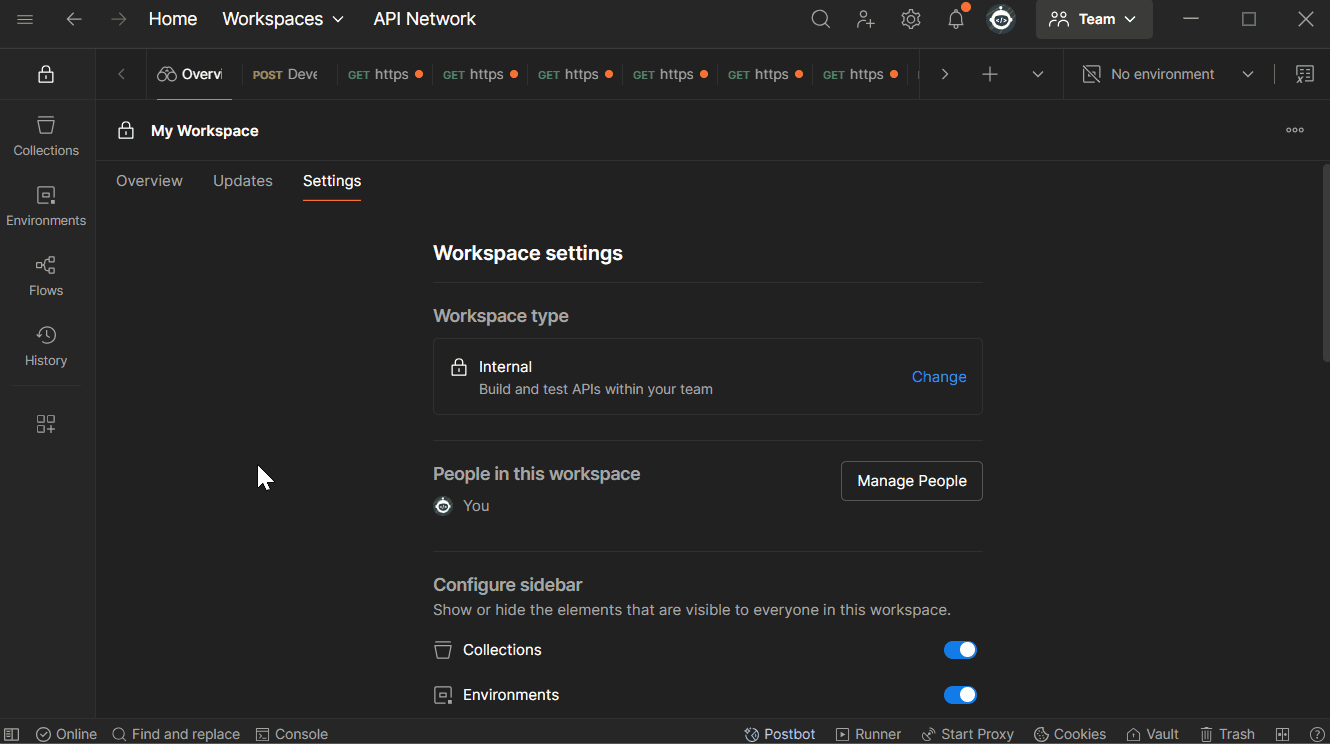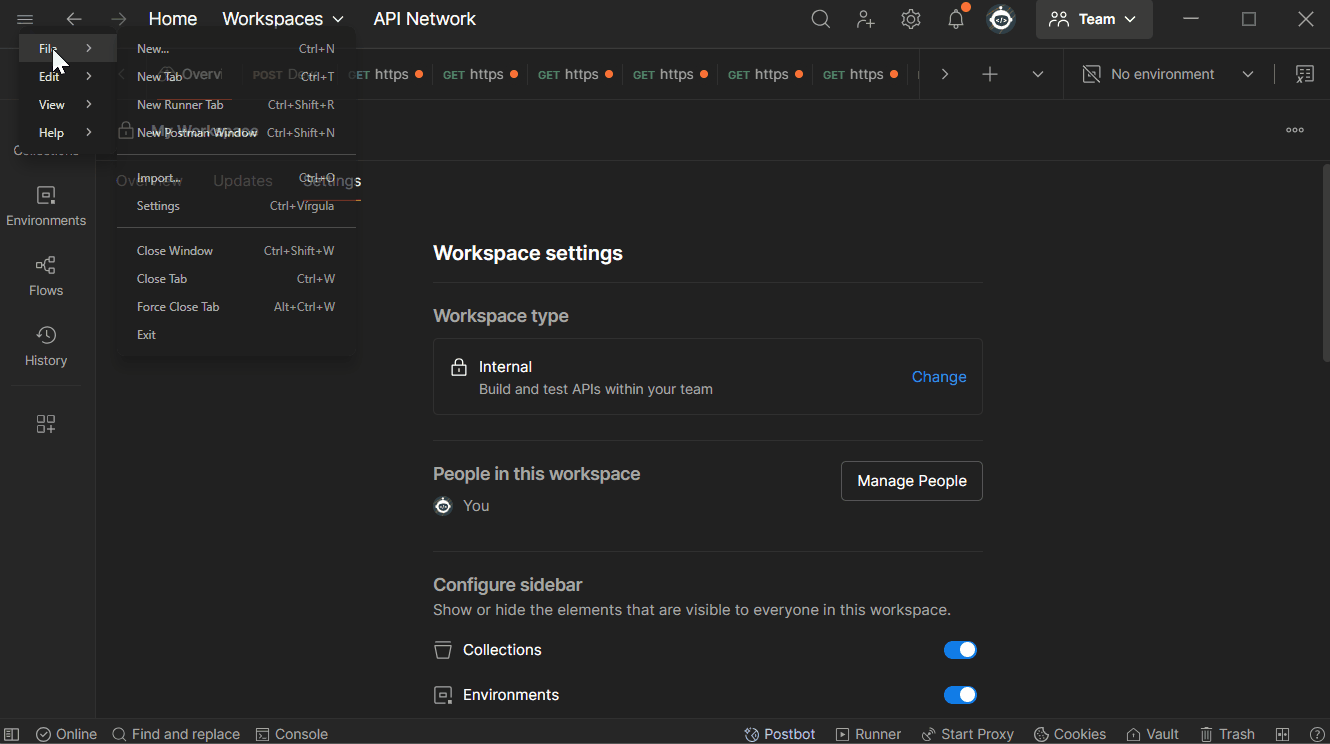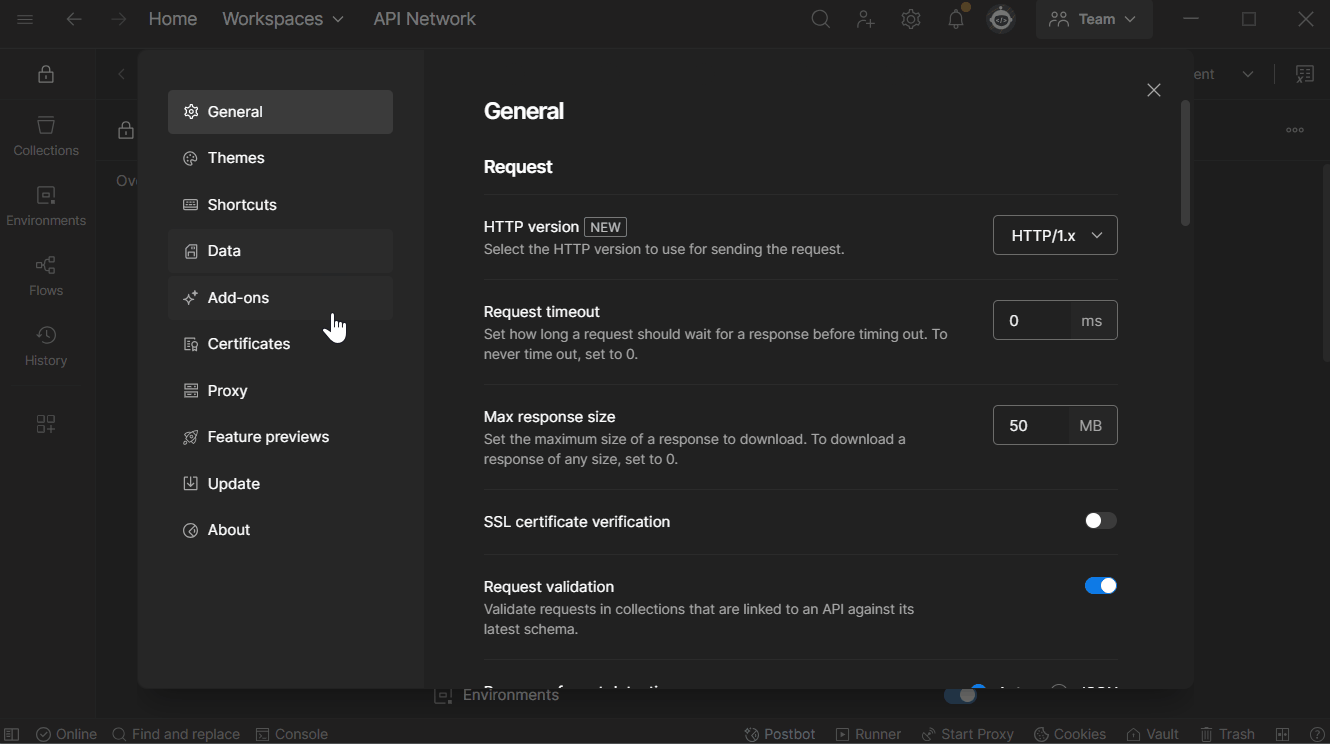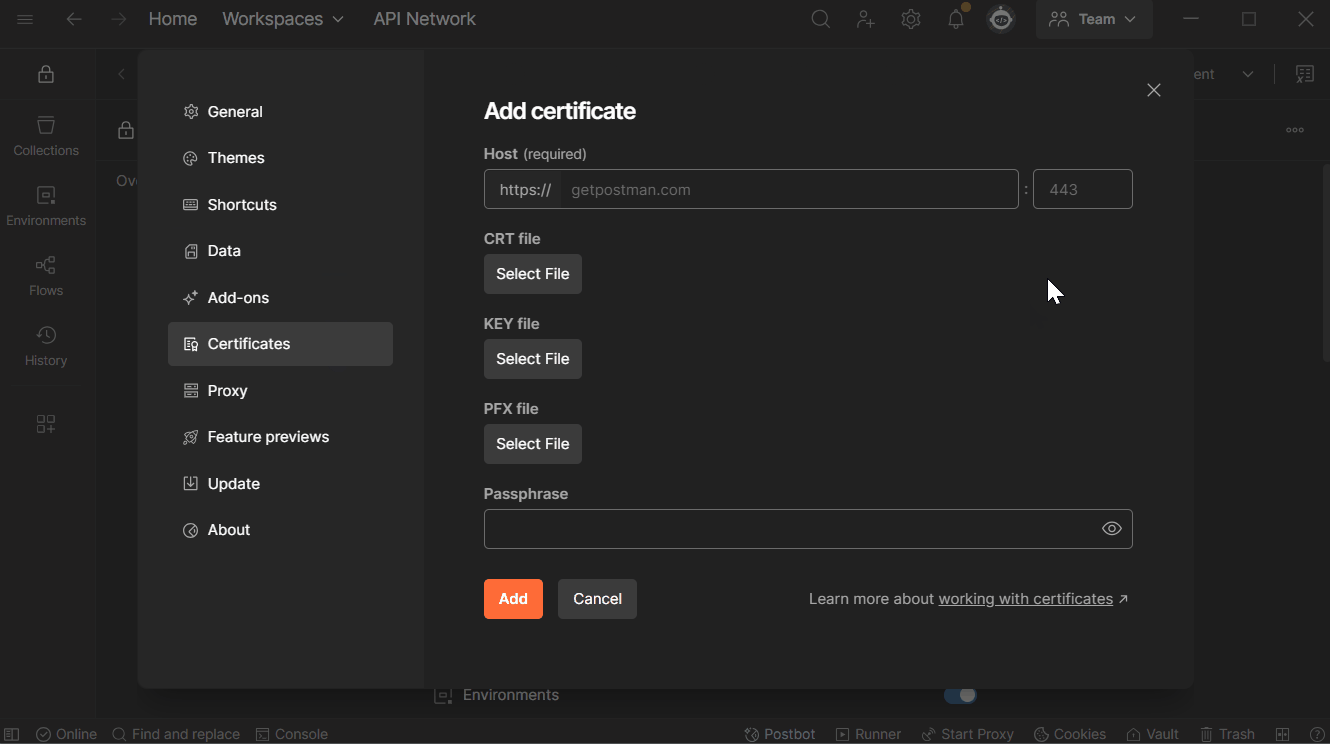
- Define the Host for the call.
- In CRT file, add the certificate file (
.crt). - In KEY file, add the private key (
.keyfile generated earlier with the CSR). - Click Add to save the certificate configuration.
Once configured, any request made to the specified host will automatically include the certificate, allowing you to test mTLS-protected endpoints.
Using cURL
If you prefer to test or integrate mTLS requests via the command line, you can use cURL to send requests with your certificate and private key.
Use the following example to authenticate a request with mTLS:
_10curl --location 'https://{{account}}.vtexcommercestable.com.br/api/vtexid/credential/validate' \_10--cert {{client.crt}} \_10--key {{client.key}} \_10--header 'Content-Type: application/json' \_10--data '{_10 "token": "{{user_token}}"_10}_10'
Replace
{{client.crt}}and{{client.key}}with the paths to your certificate and private key files, and insert a valid token in the request body.